Cyberwatch Compliance Manager
A compliance control platform that adapts to your requirements
Cyberwatch Compliance Manager helps you define your compliance objectives and achieve them, from international or personalized benchmarks.





Continuously check your level of compliance
Find out how Cyberwatch Compliance Manager helps you define your compliance goals, identify breaches and suggest solutions to increase your level of security.
Map
Get the complete and contextualized list of machines and technologies in your IT park.
Choose
Define your goals using an encyclopedia of rules from the main market benchmarks.
Detect
Continuously check compliance with your standards on your information system, and notify you of non-conformities.
Prioritize
Evaluate your compliance according to the level to be reached with the MIRE terminology (Minimal, Intermediate, Reinforced, High).
Decide
Identify your level of compliance by asset or by repository and obtain information on the benefits of the different rules tested, to make the right decisions.
Fix
Retrieve remediation aids, and Cyberwatch command lines, to save your teams time.

Complete Vulnerability Management
rules, from their detection to their correction, from the same software.

Easy-to-use interface
with a low learning curve, available in French and English.
Relevant dashboards
operational and customizable, with pre-built and modifiable models.
Flexible integration
with On-Premise / Self-hosted / Cloud-based deployment.
Update
regular compliance benchmarks.
Customizable rules
Integrate your Information Systems Security Policy by creating your own rules.
Simplify the management of your compliance
Gain visibility, define your objectives and identify the necessary actions. Make a simple and motivating action plan and help your teams to correct the non-conformities by giving them precise instructions and the basis of remediation scripts.

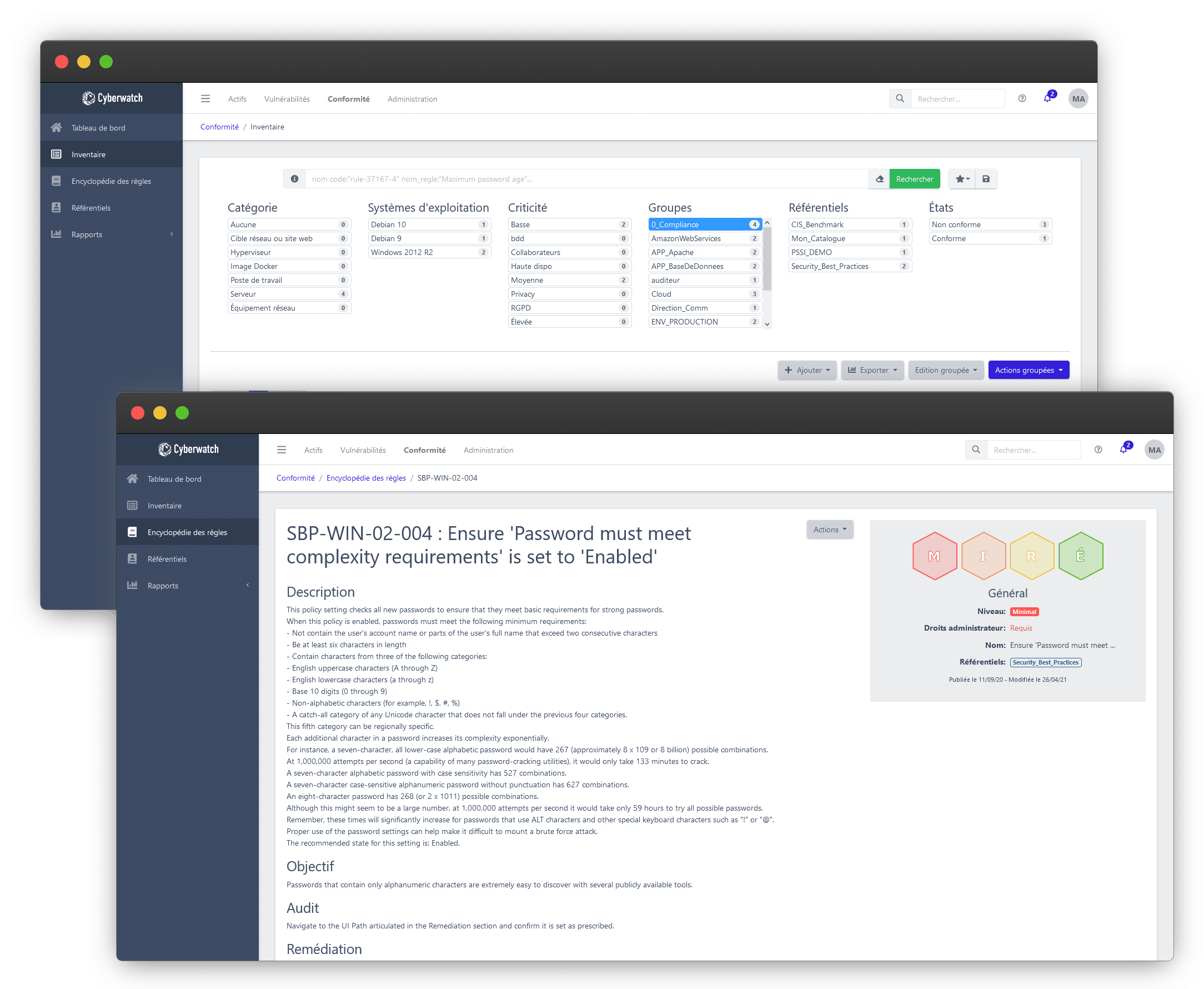
Choose a solution adapted to your Information Systems Security Policy
Cyberwatch allows you to create your own rules, via our interface or our API. You can thus translate your Information Systems Security Policy into technical scripts that will run on your machines.
Use the flexibility of Cyberwatch’s rules engine to run static code analyzes on your web applications (SAST), identify the presence of unauthorized software or the absence of a GPO.
Use standard market repositories, or create your own compliance rules
Explore our rules encyclopedia to choose the most relevant repositories for your needs, or create your own compliance rules using our customization tools.
Use our pre-built rules
to measure your level of compliance with the main market benchmarks.
Create your own repositories
thanks to our customization features, to create your own rules and compliance guidelines.
Identify the ground rules
with the MIRE classification method of the National Information Systems Security Agency.
Do you have a question?
Do you want to schedule a free demo?
Contact-us and our experts will get back to you within 24h.
Also discover our vulnerability management software
Cyberwatch Vulnerability Manager is a vulnerability management solution, with information system mapping, vulnerability detection, prioritization based on risk and on business constraints, decision support and correction module.

