A platform to monitor your vulnerabilities and your compliance, from detection to remediation, agent-based or agentless
Our platform helps you to find, prioritize, and fix your vulnerabilities and your compliance.
Get a complete view of your assets
Cyberwatch maps your information system, searches for new assets to scan, and helps you to fight against Shadow IT
Manage easily vulnerabilities in your information system
Cyberwatch detects and prioritizes vulnerabilities in your information system, and can deploy the appropriate security patches to improve your security

Check the compliance of your information system
Cyberwatch checks your assets against cybersecurity best practices, based on international standards that you can customize, and helps you build a valid in-depth defense.
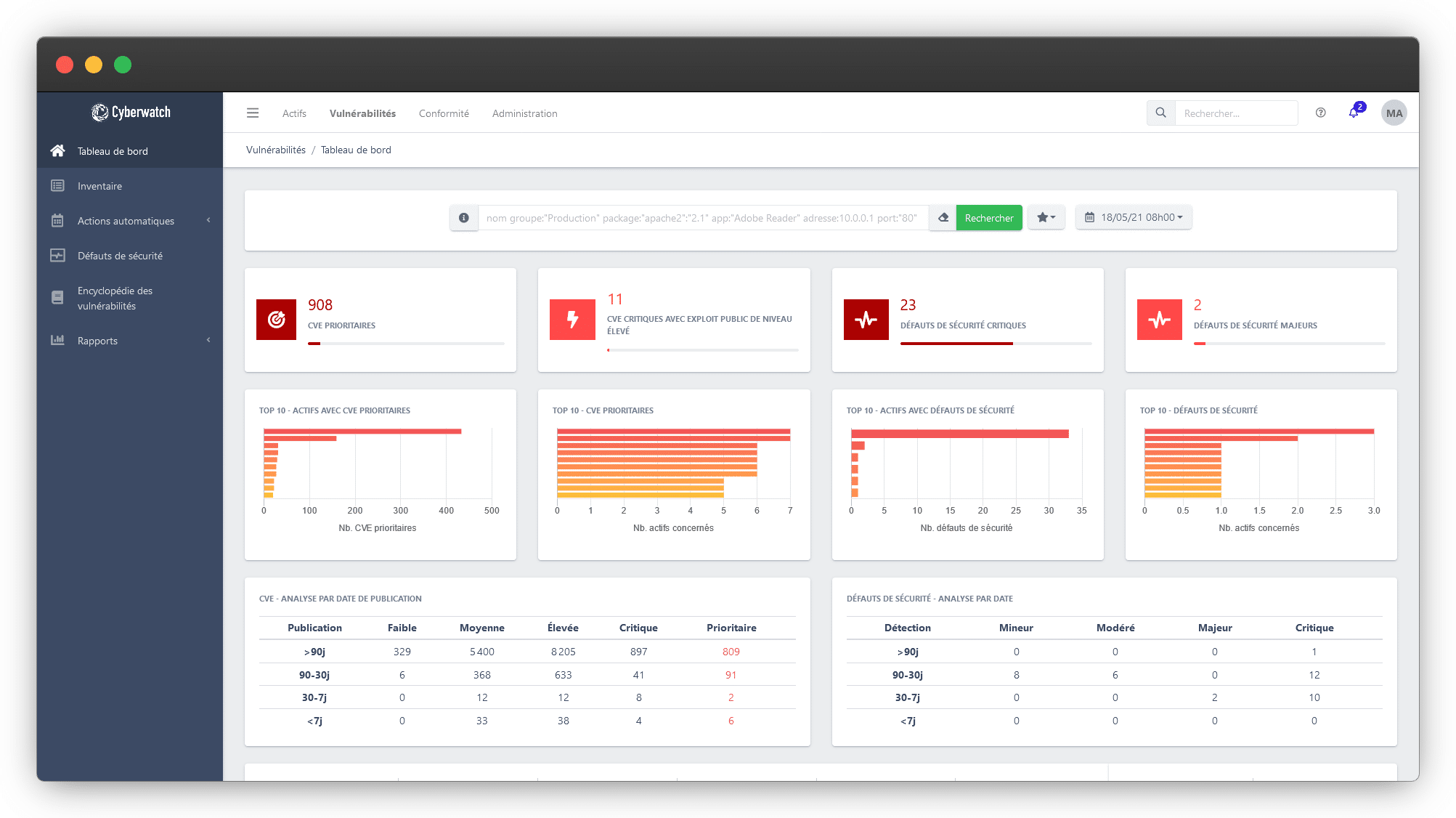
Cyberwatch Vulnerability Manager
Monitor your vulnerabilities
Cyberwatch Vulnerability Manager is a vulnerability management platform with Assets mapping, Vulnerability scanning, Prioritization based on technical risk and business requirements, Decision-making tools, and an embedded Patch Management module.

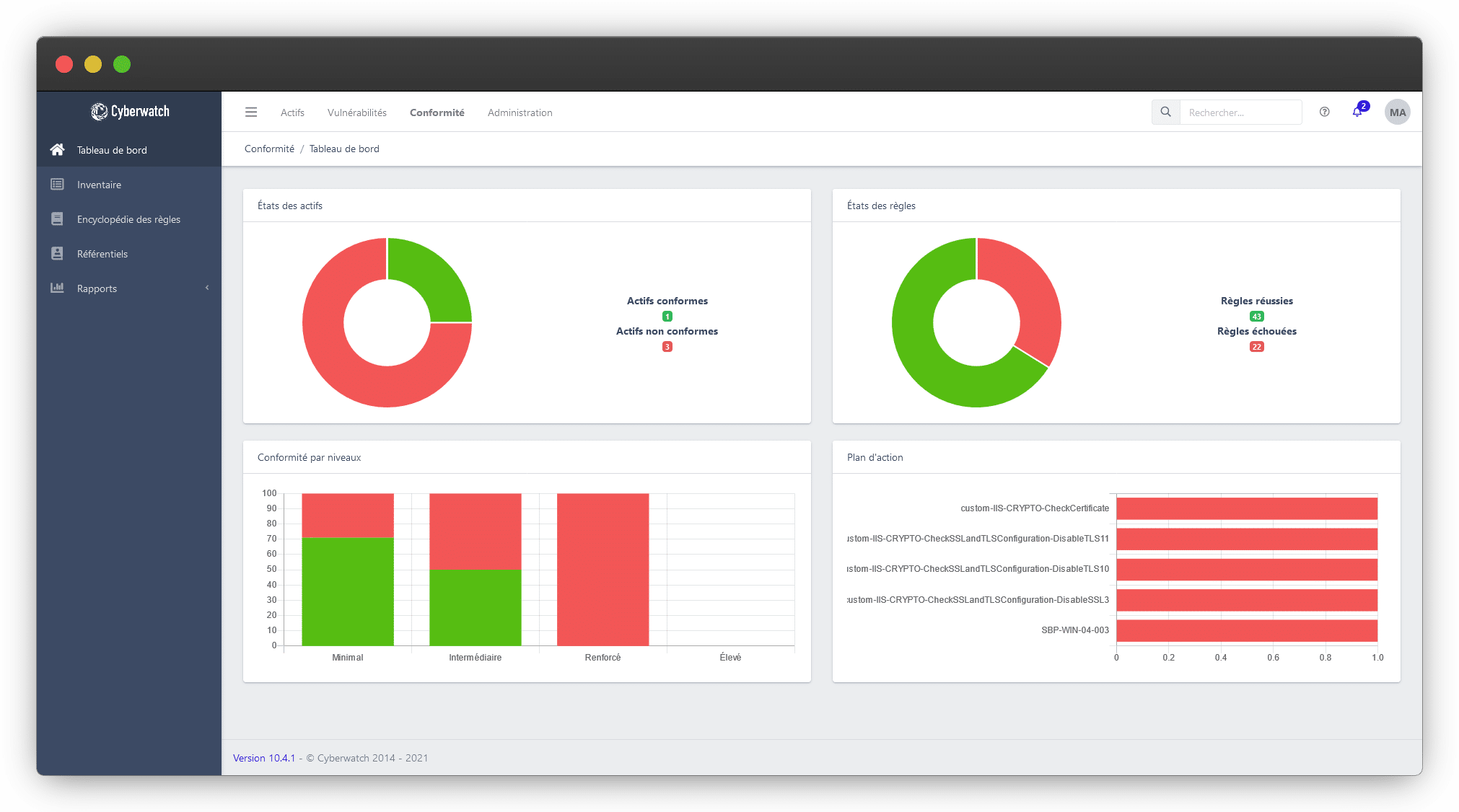
Cyberwatch Compliance Manager
Check your compliance
Cyberwatch Compliance Manager is a compliance management platform, with hardening level assessment and complete customization of available rules and repositories.
Flexible agent-based or agentless scanning options>
Our platform allows you to scan your assets in both agentless and agent-based modes, and also in air-gapped / disconnected mode for sensitive environments.

Confidential data
Our platform can be deployed in the environment of your choice and does not send your results to any third-party. The security assessments are performed in your information system. The results stay in your information system.

Continuous analysis for maximal visibility
Our platform performs continuous assessment of your assets even when they are not on your network. New vulnerabilities are automatically associated to your assets based on last available data, so that you can have maximal visibility on the security of your information system.
Do you have a question?
Do you want to schedule a free demo?
Contact-us and our experts will get back to you within 24h.
