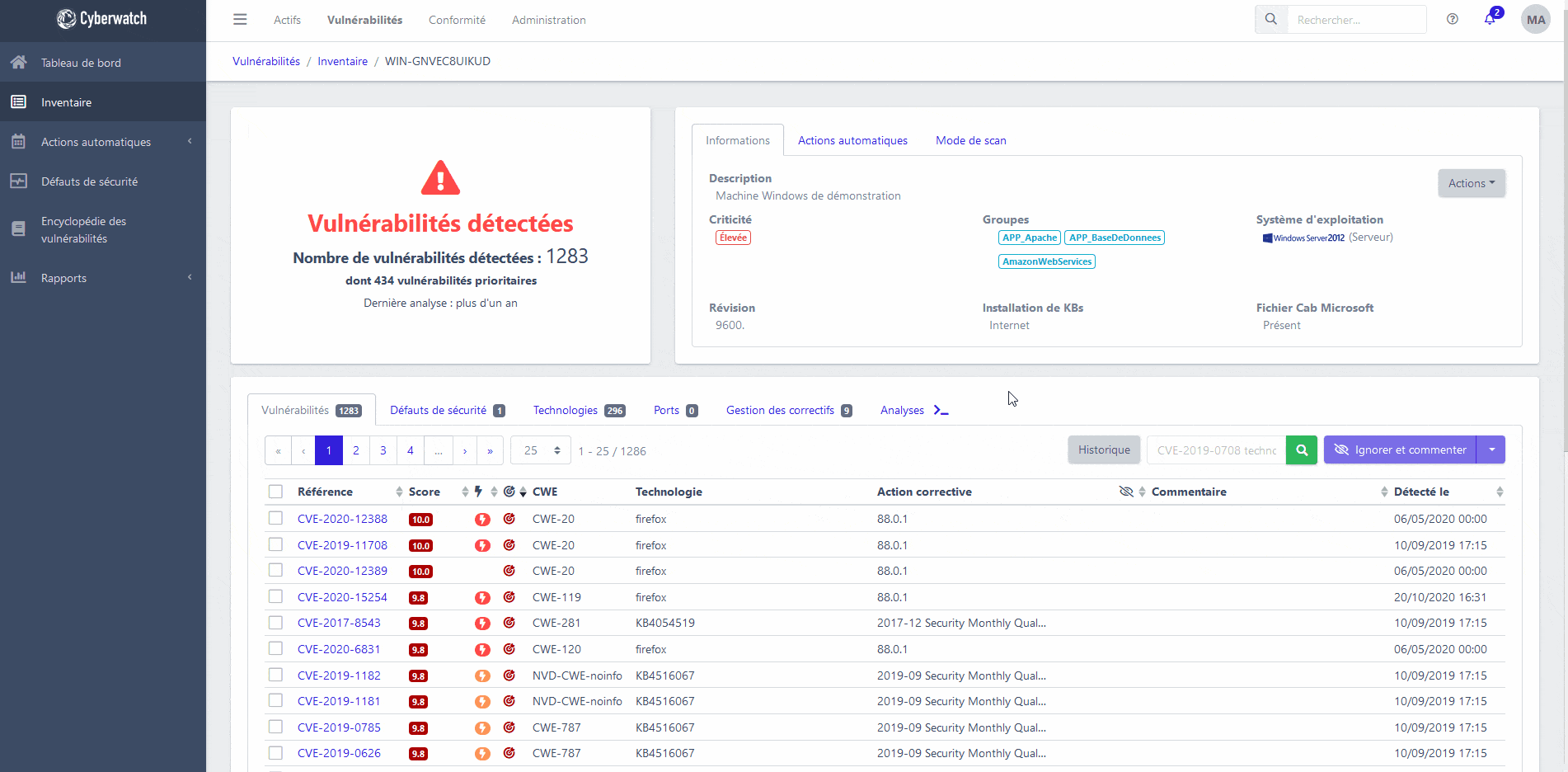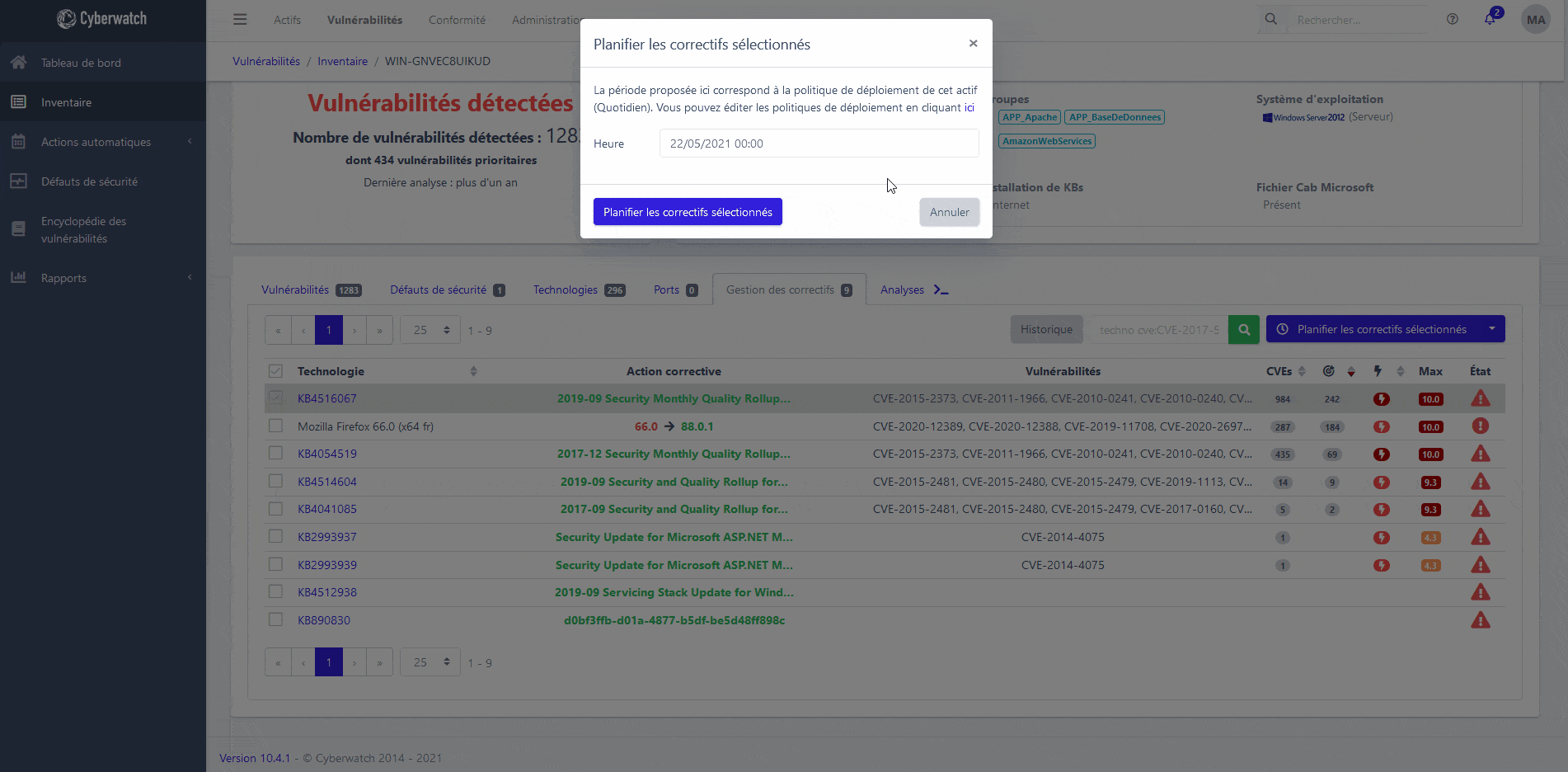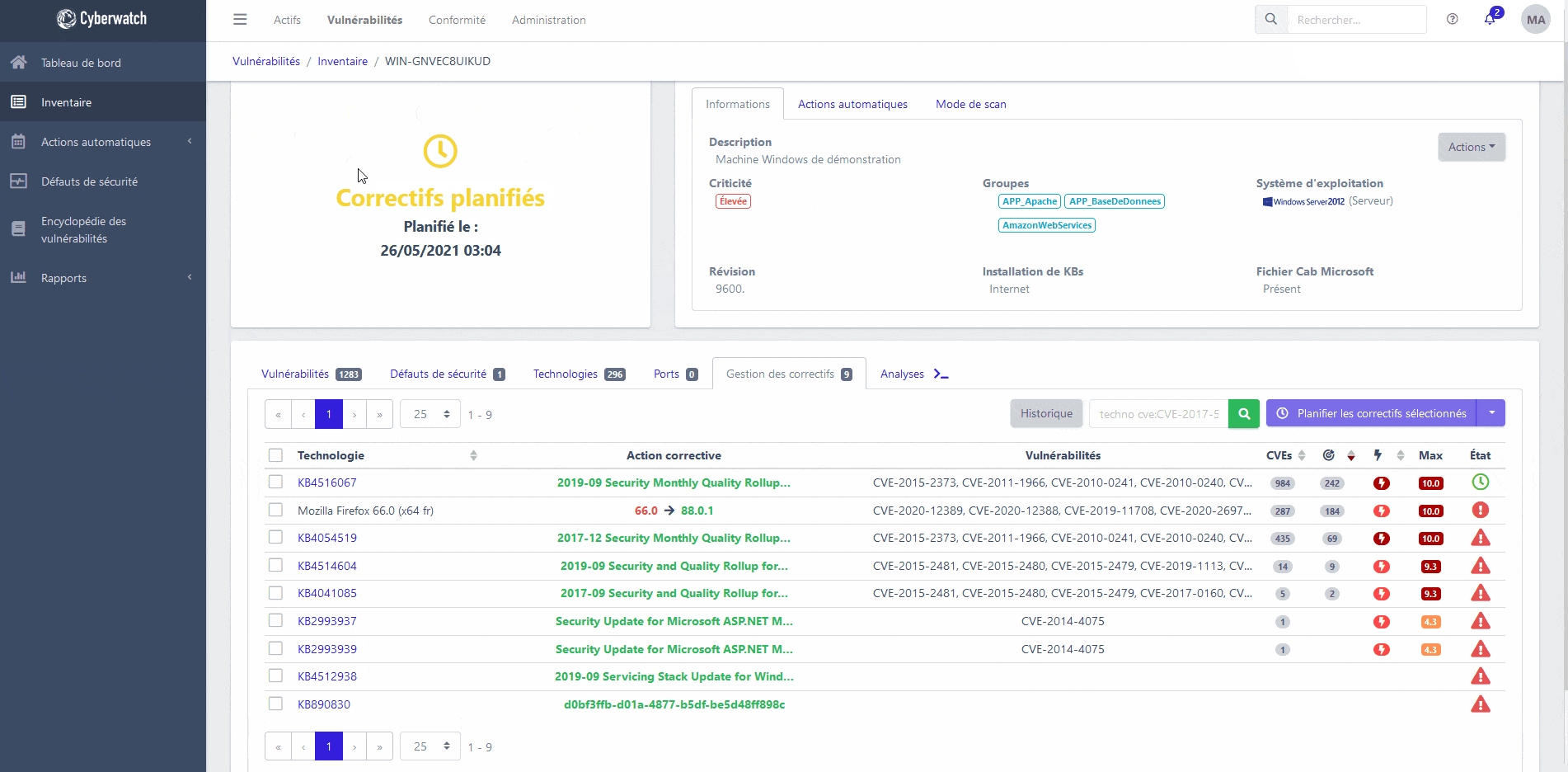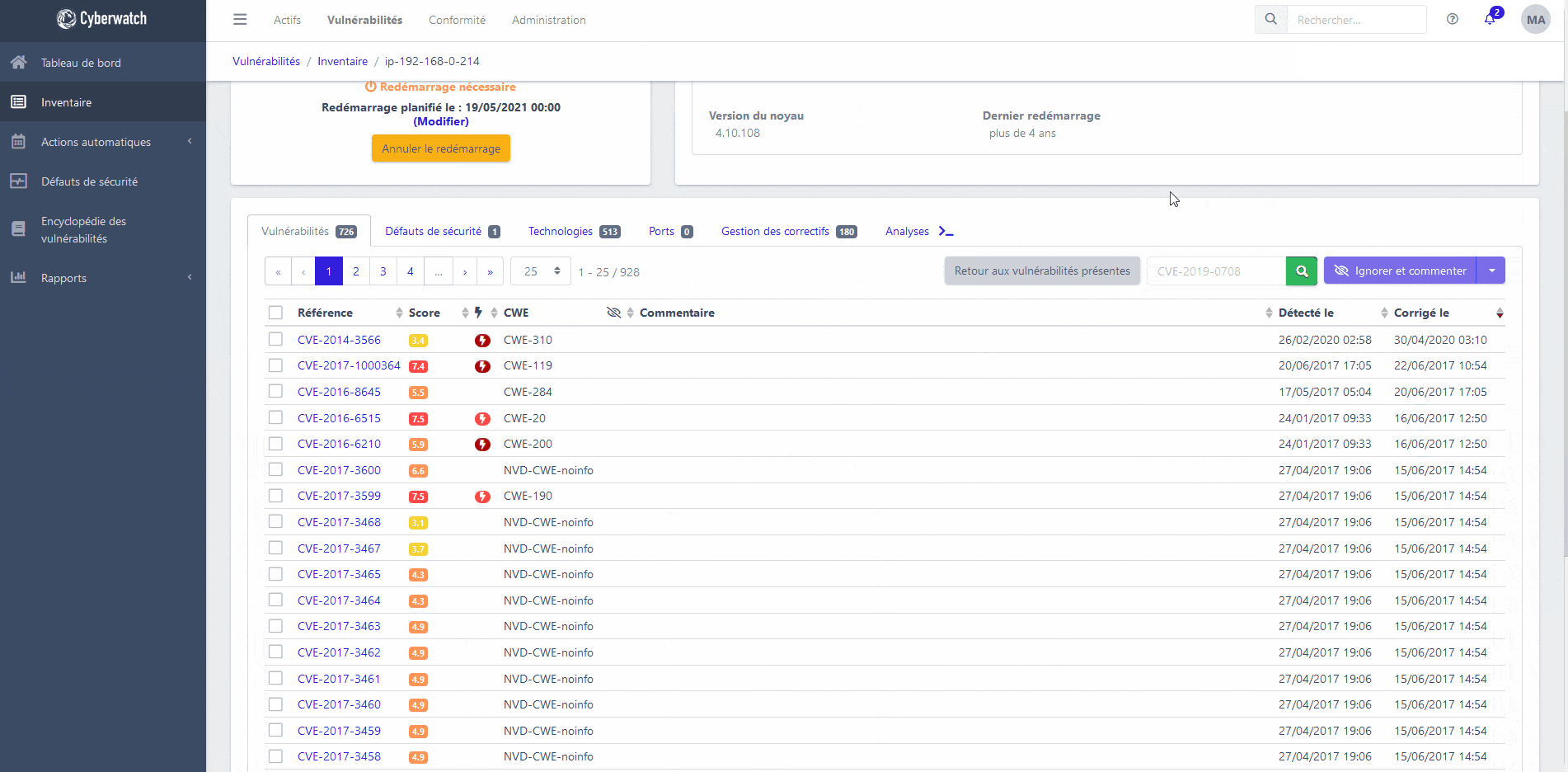
Cyberwatch Vulnerability Manager
Discover the features of our platform to monitor your vulnerabilities
Mapping
Get complete and continuous visibility of your assets
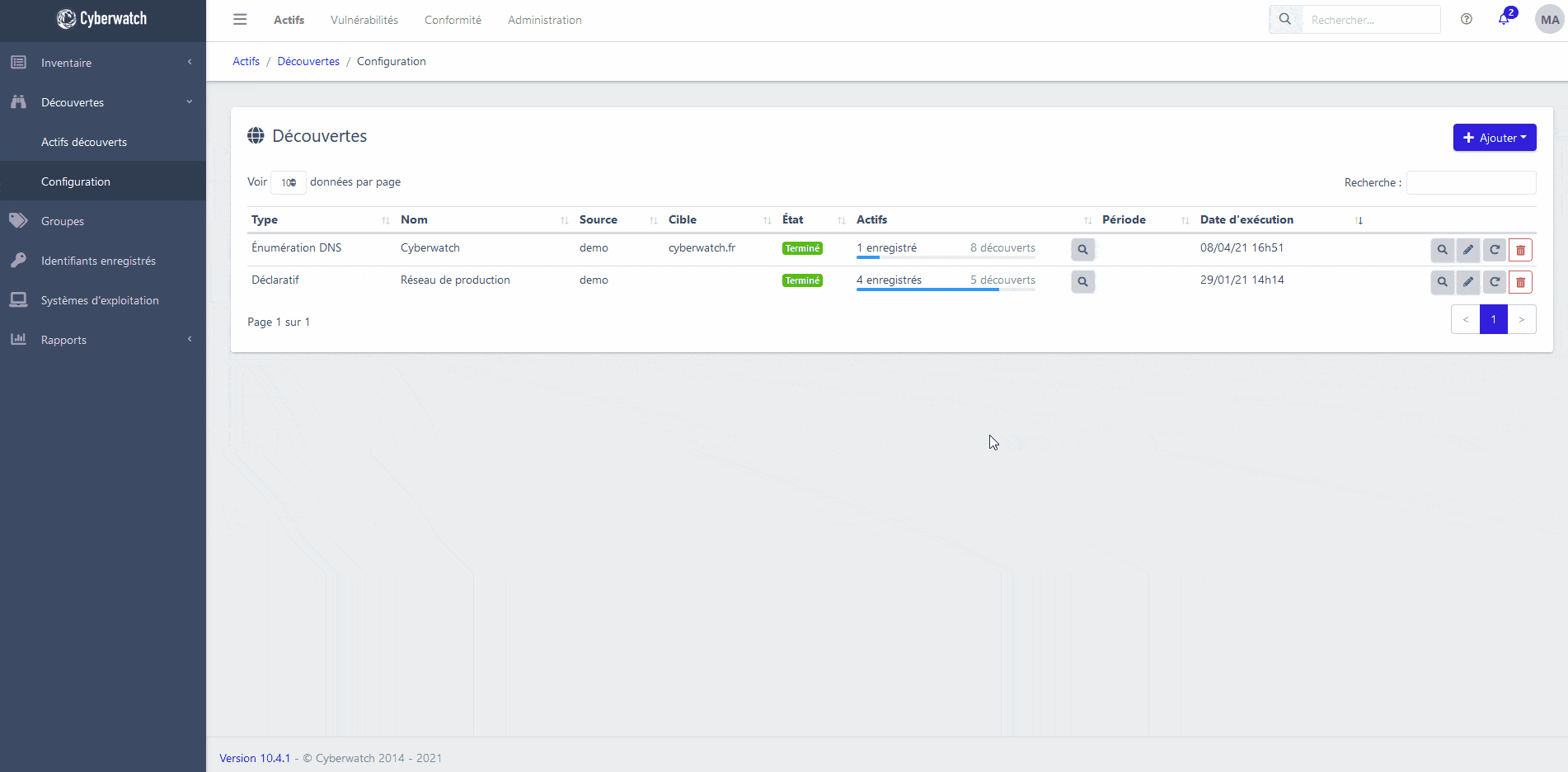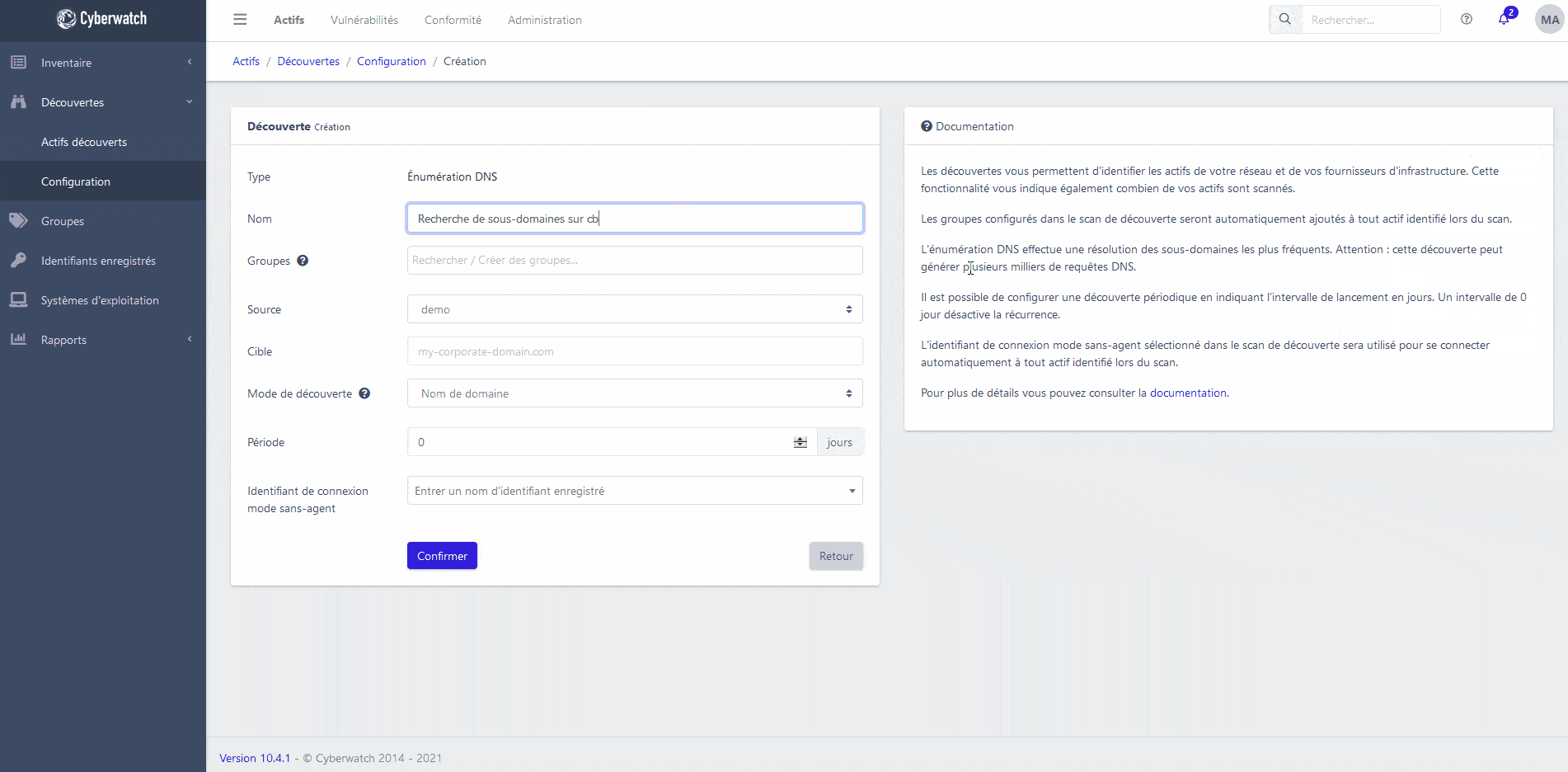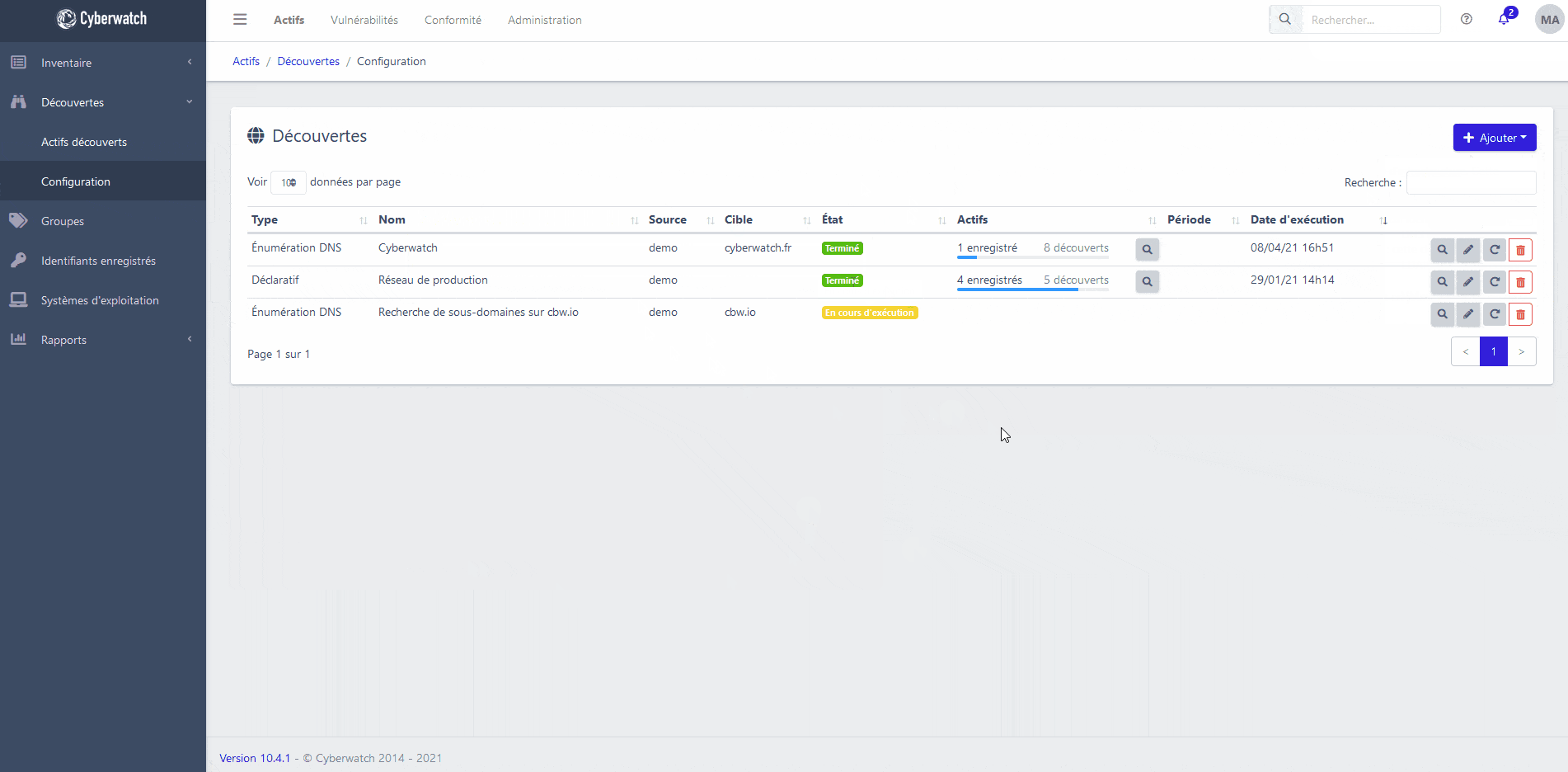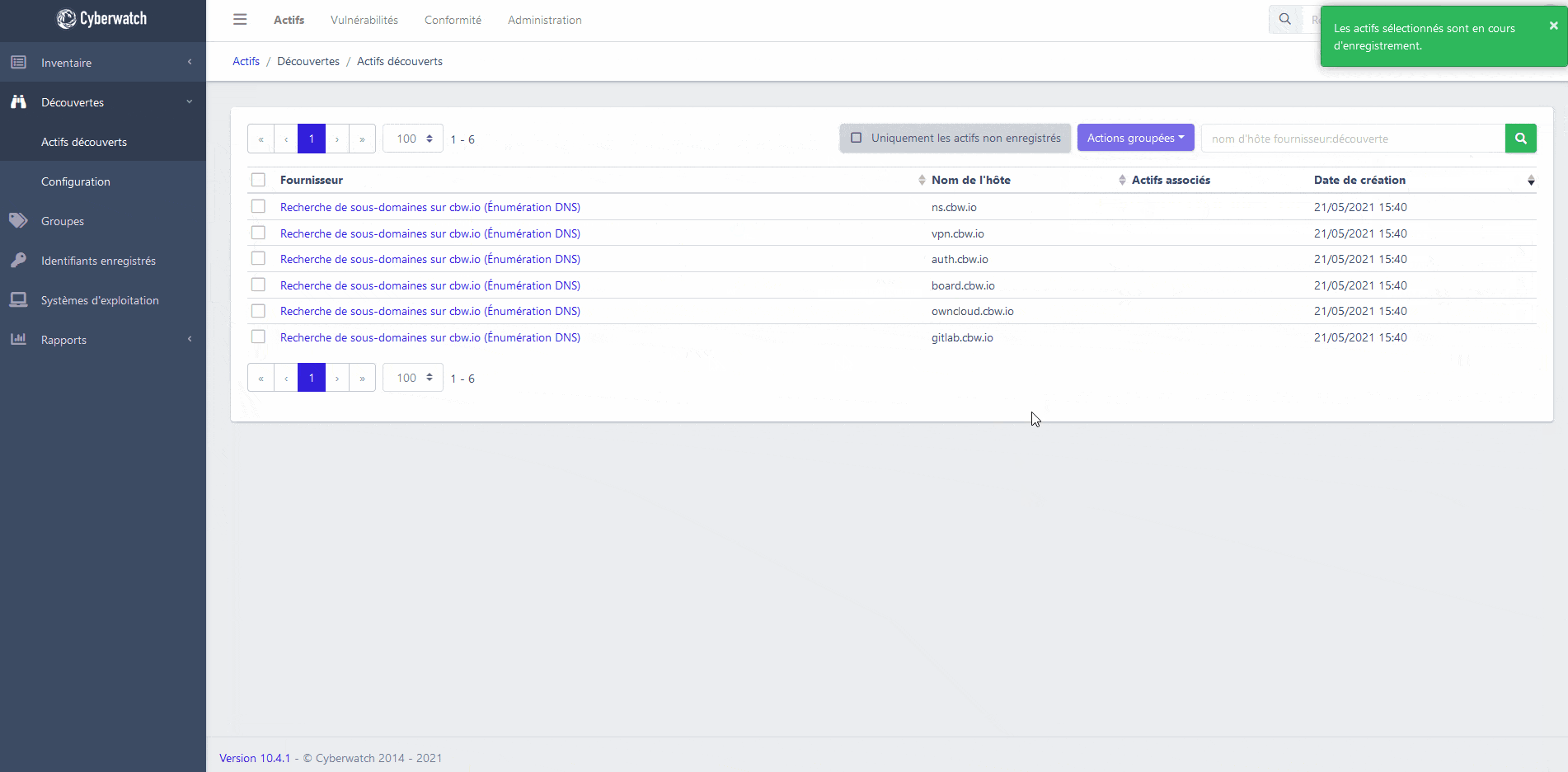
Identify the elements present in your information system with our asset discovery engine.
Regularly scan your network for Shadow IT and look for new domain names in your possession.
You can also interface our platform with your infrastructure management tools (CMDB, LDAP, Active Directory, OpenStack, VMWare, vSphere, Amazon Web Services, Microsoft Azure, Google Cloud Platform…), to cover your entire exposure area.
Detection
Scan your vulnerabilities, with or without an agent
Search for vulnerabilities in your assets using our proprietary scanning engine, which can identify vulnerabilities in over 70,000 technologies.
Run your scans with or without an agent, on your servers, workstations, Docker images, network devices or even your websites.
For the most sensitive assets, use our “air gap / disconnected” scanning mode, from data coming from a CMDB, an asset management tool (Tranquil-IT WAPT, Teclib’ GLPI, Microsoft SCCM…) or a USB key.
Identification
Identify the most important assets, according to your business challenges
Define your availability, integrity, and confidentiality goals, and create prioritization strategies that fit your needs.
Choose a vulnerability threshold, for each asset scanned. Finally, define groups to describe the environment of each asset, and provide your users with restricted access to a specific area within our platform.
Prioritization
Highlight the vulnerabilities that really matter
Our platform automatically calculates the real danger of each vulnerability for each of your assets, using the Cyberscore.
The Cyberscore is a method developed on the basis of the environmental and temporal criteria of the CVSS v3.1. It aggregates data from Cyberwatch’s monitoring of available public exploits and attack kits. It also includes data from your configured business goals and thresholds.
This way, you can easily see the priority vulnerabilities in your information system.
DECISION SUPPORT
Make the right decisions, and keep track of your actions
Generate relevant and customizable dashboards to help you make the most appropriate decisions to achieve your goals.
Monitor your vulnerabilities by asset or by outcome, and measure your remediation times.
Send requests to third party systems (ticketing tool, CMDB, email…) and add comments on vulnerabilities.
Identify vulnerabilities that you can’t address for production reasons, and mark them as accepted risks so you can focus on the things you can fix.
Correction
Deploy the appropriate patches and neutralize your vulnerabilities
Instruct our platform to install security patches from vendors to address your vulnerabilities, with or without an agent, via our native Patch Management module.
Deploy security updates on Linux and Microsoft Windows systems, according to your configurations. Our platform automatically recognizes the presence of a WSUS and your package repositories. It uses these items as sources for your updates.
Connect Cyberwatch to your existing software to patch vulnerabilities via your production tools.
Complete your risk analysis with our vulnerability encyclopedia
Check out the knowledge base embedded in our platform for additional information on vulnerabilities, with clickable links to public attack kits, vendor alerts, and government advisories.

Knowledge base on vulnerabilities, embedded in our platform
Scan with all available vulnerability information in one place.

Instantly identify assets impacted by a vulnerability
Search for the vulnerabilities you are interested in in our encyclopedia, and immediately get the list of impacted assets.
Data updated every hour
Get up-to-date vulnerability information, updated hourly with the latest information from vendors and authorities.
Do you have a question?
Do you want to schedule a free demo?
Contact-us and our experts will get back to you within 24h.